Maximum Security
 The PacketiX VPN Online Test Environment is based on the software PacketiX VPN 2.0. It uses encryption and digital signature based on the SSLv3 protocol, and offers user authentication by PKI (private key infrastructure). Within the VPN Server, all Virtual Hubs created by the users are completely separate Layer 2 segments, so information cannot be viewed by third persons. The PacketiX VPN Online Test Environment is based on the software PacketiX VPN 2.0. It uses encryption and digital signature based on the SSLv3 protocol, and offers user authentication by PKI (private key infrastructure). Within the VPN Server, all Virtual Hubs created by the users are completely separate Layer 2 segments, so information cannot be viewed by third persons.
Strong Encyption Protocol
PacketiX VPN 2.0, the VPN software developed by SoftEther Corporation and used for the VPN Online Test Environment, has a strong encryption function included. See Chapter 1.5.2 of the PacketiX Online Manual for details.
Abundant User Authentication Options
The administrator of the Virtual Hub can select an appropriate user authentication method from a wide range of options.
- Anonymous authentication
Anonymous authentication allows connection as long as at least the user name is known, and is used when establishing widely offered Virtual HUB service, etc. It is not usually used for businesses, etc.
- Password Authentication
Standard password authentication is the method of conducting user authentication by user name and password and is the method for which security can be most easily maintained. Users can also change the password themselves using VPN Client. The password is hashed when typed in and because password confirmation is conducted by challenge and response when authenticating, the password and hash data do not flow on the network.
- RADIUS server authentication
Method of user authentication using RADIUS authentication server already owned by company, etc.
- NT domain and Active Directory authentication
Method of user authentication using Windows NT main controller or Active Directory of user database of Windows 2000 / Server 2003 already owned by company, etc.
- Certificate authentication (PKI authentication)
In a Public Key Infrastructure (PKI), clients hold a private and a public encryption key. The server sends a certificate to the client, who uses his private key to encrypt it. The server in turn uses the client's public key to decrypt the certificate and verify whether the user posesses the right private key.
This method is the most secure, because contrary to a password, the private key is never handed out by the client or sent over the connection.
Separation and Independence of the Virtual Hub
At the VPN Online Test Environment, many Virtual Hubs are run by one VPN Server cluster system. This way, a high number of users can make shared use of one public server.
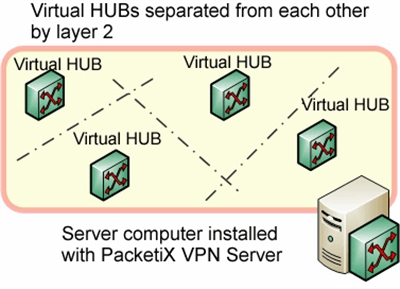
As explained in Chapter 1.4.2 of the PacketiX Online Manual, Virtual Hub, under the heading "Creation and Administration of Multiple Virtual HUBs", one PacketiX VPN Server can operate a multitude of Virtual Hubs. The separation of these Virtual Hubs is secured by embedding each in an independent Layer 2 segment.
Consequently, there is no communication possible between computers connected to different Virtual Hubs in different segments of the network. This ensures a secure environment for the Virtual Hub.
Virtual Hub administration functions
The administrator of a Virtual Hub specifies an administrator password. Without knowing the password, others can't access the administration pages of this Hub and they can't use the administration tools for an administration connection.
Administration rights to individual Virtual Hubs are separated by the PacketiX VPN Server 2.0 security functions, so administrators of one Virtual Hub can't access the contents or the configuration of other hubs.
Apart from just operating several Virtual Hubs on one public shared VPN server, with this functionality each individual Hub administrator can use the system as if operating his own private VPN Server.
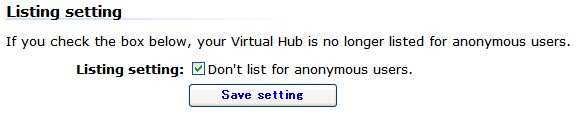
Disable public listing of the Virtual Hub
Users can display a list of the Virtual Hubs running on the VPN Online Test Environment in the PacketiX VPN Client 2.0 settings.
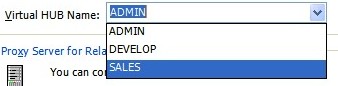
Administrators who wish to hide the name and existence of their Virtual Hub from third persons can disable the listing in the Virtual Hub setting pages.
 Back to Top of Help
Back to Top of Help
|